Last Updated on May, 2024 by Edison
This is the ultimate guide to social engineering.
Here you’ll learn:
- How to profile people through communication styles
- Why do we suck at detecting lies and deception?
- The golden rules of building rapport
- The best tools to collect information
And much more…
So, let’s get into it.
DISC Profiling
As a social engineer is crucial for you to understand yourself and others because building rapport and influencing people becomes easier.
A good framework that helps in understanding people is DISC
It shows four communication styles: Direct; Influencer; Steady; Conscientious
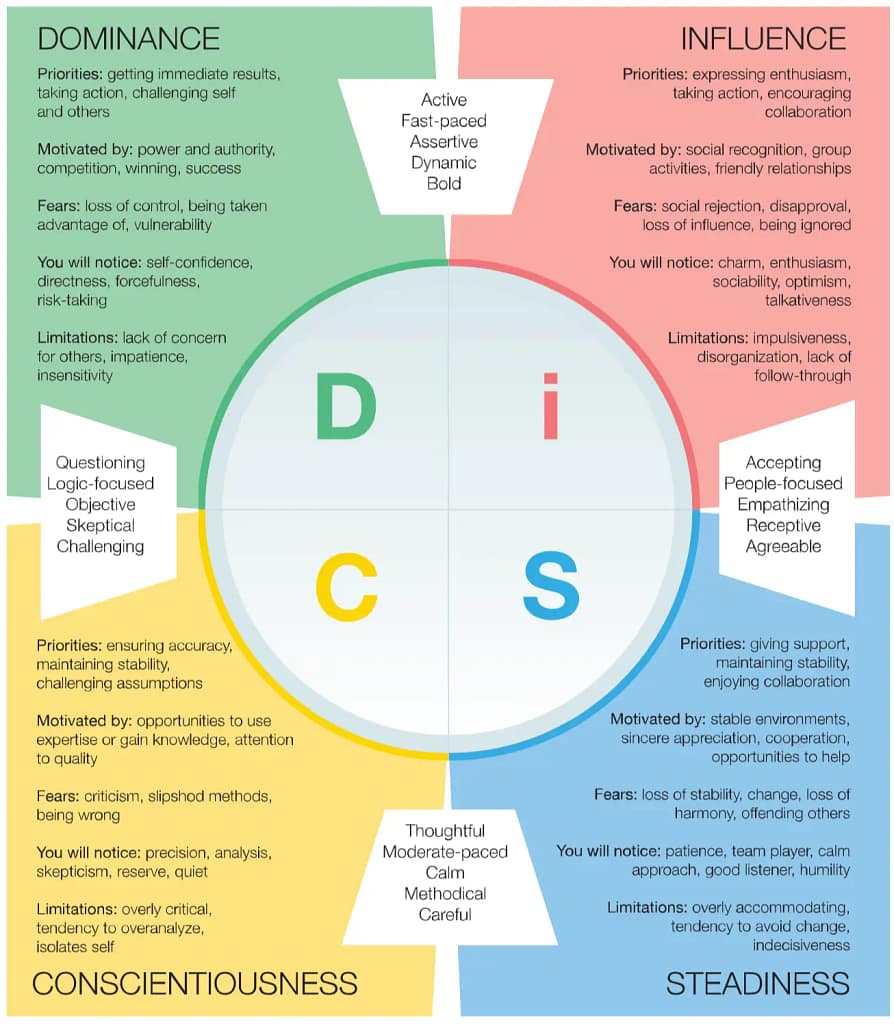
Now, we all exhibit each one of the communication styles. But one style is more pronounced than others.
Understanding your style will help you become aware of your strengths and weaknesses.
And it will help you adapt to their preferred style.
For example, if you are an influencer, you might find it challenging to build rapport with a conscientious person. You might even find them boring. Because you are talkative, you express your emotions while they are reserved and favor logic over emotions.
When you are with a person who prefers another communication style, ask yourself, “What kind of behavior do they exhibit the most and what kind of behavior might put them off?”
It will take lots of practice to become like a chameleon – able to adapt to any style without even thinking about it. To become unconsciously competent in this.
Truth Default Theory
When we communicate with others, we tend to presuppose they are honest.
In social situations, we don’t think like scientists… slowly gathering and analyzing evidence before concluding. We do the opposite. We start by believing.
You can have doubts about someone and still believe him.
But we stop believing only when our doubts rise to the point where we can no longer explain them away.
The upside is that what we gain in efficient communication is far more valuable than the cost of being deceived occasionally.
How good are people at distinguishing truths from lies?
Slightly better than chance.
We think that the better we know someone, the more we can understand when they’re lying. And we also think that they wouldn’t lie to us.
Being close to someone will make us truth-biased.
What about their nonverbal behavior?
People look at a group of behaviors when trying to distinguish truths from lies.
Timothy Levine, the co-other of Truth Default Theory, in the book, Duped wrote:
People are more likely to attribute deceit to speakers who avoid eye contact, shift posture more often, take longer to respond, talk faster, make more speech errors, have more pauses and hesitations, have less plausible content, contradict themselves, are less conversationally involved, convey uncertainty in their voices, are less friendly and cooperative, and act nervous.
If you seem anxious and uncertain, you’re more likely to be doubted, even if you are telling the truth.
If you appear friendly, confident and engaged, you’re more likely to be believed, even if you are lying.
Keep these in mind when pretexting.
Build Rapport
1. The friendship formula
Proximity – People who share physical space are more likely to become attracted to each other, even if no words are exchanged.
Frequency & Duration – The more time you spend with that person, the more you can influence them.
Intensity is how strongly you can satisfy someone else’s psychological and/or physical needs through verbal and nonverbal behaviors.
Proximity + Frequency + Duration + Intensity = Friendship
2. Artificial time constraints
Have you ever been sitting in a bar or a library when a stranger tried to start a conversation with you?
Did you feel awkward?
This discomfort comes from not knowing when or if the conversation will end. So, the first step in developing rapport is letting the other person know there is an end in sight and is close.
You can do that by mentioning the time or having body language that shows you are leaving.
e.g. “Hi, I was about to leave in a second, and I am very sorry to bother you, but I was hoping you could help me…”
3. Accommodating non-verbal’s
Give a genuine smile; slightly tilt your head and lower your chin.
Also, if you stand toe-to-toe with a stranger, it might intimidate them. Instead, keep your body and legs slightly at an angle.
4. Speak at a slower rate
Speak slowly so people can understand your words and appear more credible. And try not to use word fillers such as “um,” “uh,” or “like.”
5. Sympathy or assistance
Making a simple request is a great way to develop a quick rapport.
The requests must be very “light” if you’re talking to a stranger. In general, you can ask for advice on a particular topic.
6. Ego suspension
It is the most effective technique to build rapport. But it’s also tough to make it work.
Let’s define ego suspension…
It is letting go of your ego – the need to be first, correct, or perceived as smart.
Ego suspension requires you to consider someone else’s thoughts, statements, and opinions, even if you disagree.
Reminding yourself of the ultimate goal is a great way to suspend your ego and keep your emotions under control.
Let’s say that your target says something that hurts your ego. You can fall into the trap and respond negatively to him – an action that might break rapport.
Or, you can remind yourself that your goal is to build rapport and elicit information, so it doesn’t matter what he says about you or what you care about.
7. Be nonjudgmental
The problem with judging people is that we make assumptions about why they behave in a certain way.
And often, our assumptions are wrong and what’s even worse, we stop trying to figure out the real reason behind their actions.
Consequently, we will probably hurt them and damage their relationship with that person.
We need to resist the urge to correct if we think they’re wrong.
We need to show respect and a complete understanding of their ideas and choices in life.
8. Quid pro quo
You give a little information about yourself to make them comfortable opening up.
There are two types of situations where you might use it:
- The other person is very introverted.
- They suddenly realize how much they have been speaking and feel awkward.
9. Be aware of unconscious communication
Albert Mehrabian, a researcher in the 1950s, found that the total impact of what we say is:
- 7% verbal (words only)
- 38% vocal (tone of voice)
- 55% nonverbal
This doesn’t mean that words don’t matter, but that we are also communicating with tonality and body language.
As you know, we can give different meanings to the same word by just using our tone of voice. And you can guess how someone feels by looking at their body language.
So, you need to use the elements in a congruent way.
If you say something, but your tonality and body language give a different message, then people will get a gut feeling not to trust you.
Align the three elements, and you will influence people emotionally and logically.
Phishing
It is one of the most common social engineering techniques that attackers use today.
How does it work?
You send an e-mail that appears to be from someone you know or a company. And you incorporate fear or a sense of urgency to manipulate targets to act fast.
In addition, you use links or link shorteners to redirect targets to malicious websites through URLs that may appear legit.
You can also clone a website to look more legitimate and trick people into entering login credentials.

In my video, I explain how you can create a phishing site for security purposes [03:03]
Why phishing works?
Two simple reasons are that social engineers or scammers exploit greed or gullibility.
Greed – Most people don’t think straight when “offered” large sums of money. It’s like believing you have a real shot at winning the lottery.
Gullibility – Many people fully trust others, especially strangers. And this can put them in an unsafe position. Others are uneducated about the dangers of phishing.
Examples:
The Amazon scam is prevalent. It doesn’t use your name, and you can see it’s not legitimate by looking at the URL.

The PayPal phishing

Spear Phishing
It’s sending emails to someone to seek unauthorized access.
For example, you can target someone who deals with many emails daily, such as a recruitment consultant.
You can send an email having a malicious CV attachment.
They receive similar emails regularly and are more likely to open them.
You can state that you’re looking for a job and ask your CV to be kept on record if a position becomes available.
Or, if you need to send a phishing email to someone in the sales department, your bait could be a promising lead.
Hi John
I don’t have time to follow up on this lead, so do you want it? The client is very interested in our services. And it sounded like a great opportunity.
http://companyname.com/contact
If the bait is good enough, the target won’t think about the message’s legitimacy as long as the rewards are too good.
Pressure
This technique is easy to understand but very difficult to make it work.
You apply pressure to the target in a negative emotional state and then present a straightforward solution to remove the emotion.
Example:
We want to trick an employee into browsing a malicious website.
Pressure: The receptionist is contacted by the IT department, who says, “Hi Anne, unfortunately, we’ve detected that the computer you’re working on has been used to browse, well let’s say… indecent websites?”
Anne says, “How dare you! It wasn’t me”.
Solution: We respond with, “Hmm… well there are filters that should block any sites like that, perhaps your PC has been compromised? Could you browse a few company sites for me so I can check the traffic and find out what’s going wrong?”
Useful Sites
Your goal is to find as much information about your target as possible. Even the slightest detail can lead to a successful social engineering breach. So here are some sites that can help you gather information.
Pippl; Yasni; Melissa – Find someone’s presence on the internet.
Analyzewords – Analyze a person’s Twitter account based on the language used.
You shouldn’t expect to know the real personality of that individual. The reason is that most people communicate differently online than in person. But, many attacks occur based on the “online” personality.
All My Tweets – It provides a clean display of all the tweets in a post.
DomainIQ – It gives hosting information about any site.
You can use TinEye to do an image search.
Remove bg – It helps in removing undesired effects from an image. This can lead to better results when doing an image search to identify a person or an object.
suip.biz: It generates domain variations for URL hijacking and phishing.+

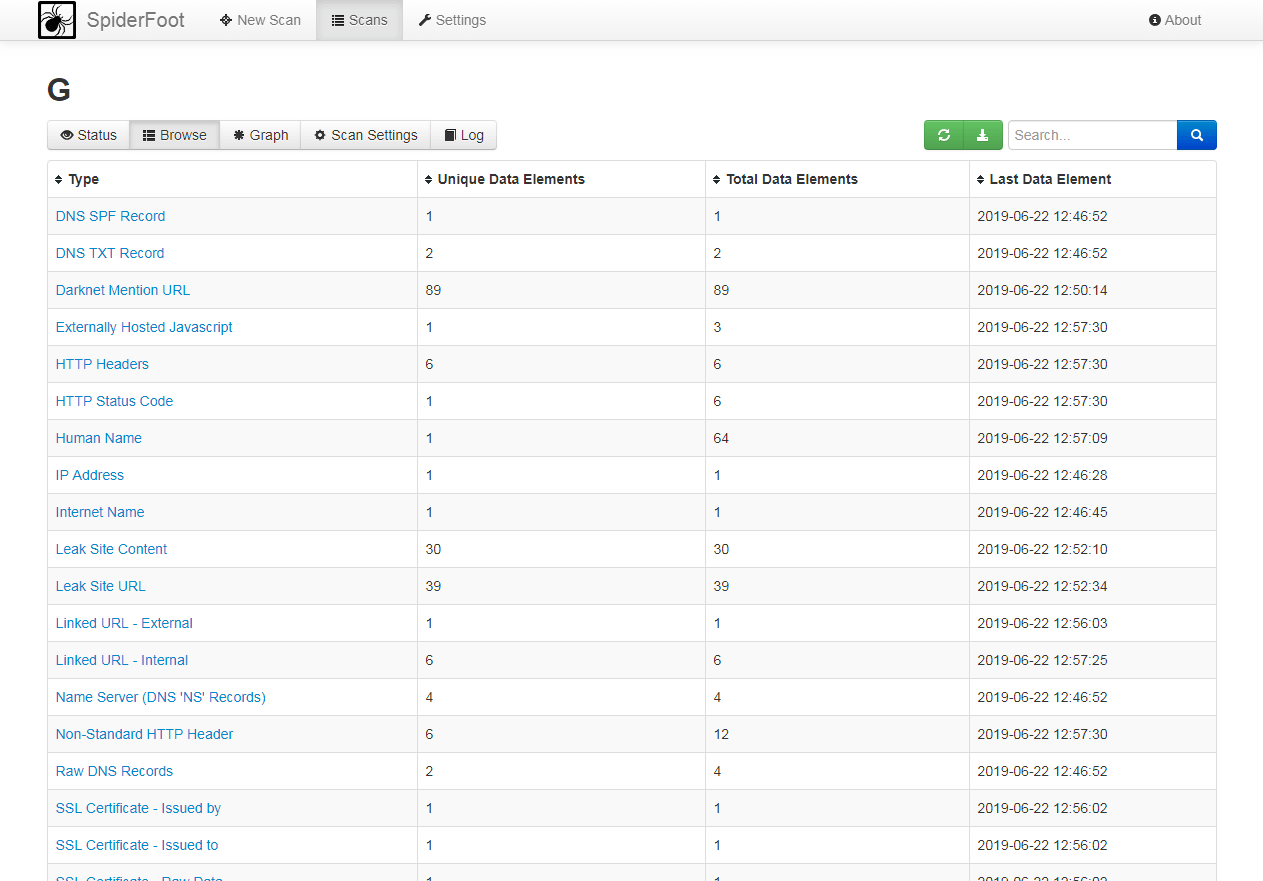
SpiderFoot is an open-source tool that provides a wide range of information, such as web servers, netblocks, and email addresses. You can download the program from the official website for Windows or Linux.
To run a new scan, you need to provide a name, and a target, check the modules, and click “Run Scan.”

An example of the information you can find:
Google Hacks
It’s one of the most sophisticated algorithms on the planet. And many Google search tricks will help you collect more information about the target.
Here’s a list with google operators:
intext: Returns a chosen word or phrase.
Site: Locates files from a particular site.
inurl: This operator restricts the search results to pages that contain a specific word in the link.
For example, inurl:Citrix/MetaframeXP will show you different organizations using Citrix Metaframe set up for their remote access.

If our target is a website with “.org” or “.edu” we use:
site: edu|org + inurl:”faculty_login.asp | .php”
filetype: Followed by a file extension (PDF, DOC, XLS) returns specific files.
e.g. confidential business plan filetype:pdf
cache: Find a copy of the page that Google indexed even if the pages are no longer available. You can also use archive.org, also known as the Wayback machine.
info: It will present information that Google has about a webpage
intitle: operator looks for documents where the specified word is in the page title.
e.g. If you want to find an MS Word document with the marketing plan phrase, you can use the query
intitle:”marketing plan” filetype:doc.
{Street Address}
You can enter a full street address, city, zip code, or state, and it automatically gives you street maps.
Google Hacking Database
GHDB was started by Johnny Long, who also wrote many books on this topic. It is a compiled list of common mistakes web/server administrators make, which can be easily searched on Google.
Dumpster Diving
It’s simply going through the target’s trash, looking for information that might be useful.
You can do this in different methods. One is to investigate the area, sneak in and dig through the trash.
The other is through the impersonation method. You dress as if you work for a waste removal company. And this gives you the pretext to get into the dumpster in a secured area.
Is it legal?
In most places in the US and UK, you can go through the trash cans without worrying about breaking the law.
However, most corporate dumpsters are located on private land.
They might not have strong security, but you should treat them seriously.
Your goal should be to get in and out as fast as possible.
Bring a couple of large bags, take what you can carry, and do the analysis elsewhere.
What are you looking for?
- Employee info – Any information that can help the attacker pretend like an employee.
- Network Maps – Information about the structure of the internal network can be valuable, such as IP addresses and ranges, server names, operating systems, distribution, and vendor names.
- Billing documents – These reveal the clients. And you can pretend to be a business partner or a client.
- Signatures – CEOs, department heads, accountants, and office managers.
- Shredded Paper – When the paper is fed into the machine and isn’t mixed, the paper strips stay close. You can use a tool like “The Unshredder” to reconstruct it.
Hacking 2FA
Two-factor authentication is a safe way to protect your access to particular websites.
It adds a second step to logging into an account, making it hard for unauthorized users to break in.
But it’s not unhackable.
I loved this metaphor in a StackExchange answer:
“Social Engineering is like water. It will find the point of least resistance and work its way in.”
Here, the weak point is the user.
How can a social engineer bypass 2FA?
First, he might know the username and password. Then he sends a warning message to the user.
It might be something like, “Your account has been accessed by a suspicious IP address if it isn’t you please reply with the verification code sent to your phone number.”
If the user responds to the fake message, the SE could bypass 2FA.
Second, the hacker has no data. He doesn’t know your username, password, or phone number.
As in the examples above, he will create a fake website with a slightly changed domain.
Then he emails, persuading you to respond and steal your 2FA-generated credential.
Tailgating
Tailgating is following an authorized person into a building.
Here’s a real-life example from the excellent book “No Tech Hacking” by Johnny Long.
Years ago, I was tasked with a physical assessment against a state government facility.
The facility was split into two areas: an open area for public and one restricted area for employees.
Both areas were connected but there was an armed guard. The front door of the restricted area had also one guard.
To make things worse for my team there were armed guards in marked vehicles patrolling the parking lots.
We’re discouraged by the heavy security until we saw a group of employees chatting while having a smoke.
I immediately knew we had found our way in.
We headed to the nearest gas station and bought a pack of cigarettes and a lighter.
I was prepared to come in as a phone technician. I wore a white T-shirt with a phone, wore cruddy jeans and work boots. And I had a company badge clipped at my collar.
Now approaching a group of smokers would have been a bad idea. If they watched me coming from the parking lot, they would consider me an outsider.
But, If they came out of the building and find me there, they would assume I had come out of the building for a break.
After the group of smokers headed back inside, I hurried to the side of the door and lit up a cigarette.
Then two employees came out and were conversing to each other.
I nodded casually and joined their small talk. They were talking about company politics and I was making sure to blow up the smoke to convince them I am a smoker.
I grunted about how the phone system had been acting out lately. They laughed and agreed.
As they put out the cigarettes, they swiped their badges to return inside.
I did the same thing and held the door open for them. They thanked me for the kind gesture and I filed right behind them.
Prevent Social Engineering Attacks
There are some ways to prevent SE attacks.
1. Suspect everything that seems to be out of the ordinary. Especially calls from people who tell you there is a severe security problem in the company and you need to give them log-in credentials.
2. Think before you click. As I explained above, email phishing is prevalent. So check the sender’s e-mail address and look where the link will lead you.
3. Physical security. Make sure that the dumpster is in a gated area. Set up authorization or identity checking at entries to a building. All entrances, not just the front door.
4. Raise awareness. Everyone in the organization should know the techniques of social engineering.
5. Delete metadata from the images you posted online.
Many photographs contain metadata such as
- The coordinates of the location where the photo was taken
- The model of the camera
- It also contains the date and time someone took the photo.
6. Always use a VPN when loging into free Wifi.
Free WiFi is unencrypted and unprotected. A hacker within a certain range of wifi networks can spy on your data.
Taking the above-mentioned steps will improve your security at home and work, but you should also be careful when using your bank card at the ATM or while shopping at stores.
Skimming
Thieves can put a card scanner on the little slot where you insert the card and copy personal data from the card’s magnetic strip.
These are called skimmers and can be bought on the black market.
In addition, thieves can install a small camera to capture footage of your pin. They might even buy number pads to overlay the original number pad.
So look for tampering at the ATM – Push and pull parts to see if there is another piece attached to it.
Look for small holes around because there might be a hidden camera. And cover the hand while entering the pin.
Try to avoid ATMs in dark and isolated locations. Instead, use an ATM inside the mall or the bank because it is much more secure.

Electronic pickpockets
Do you think your credit cards are safe in your pockets?
Well, think again.
There are devices that can steal card information without even touching you.
All they have to do is place your device near the wallet and that’s it.

To protect yourself you can buy what’s called a shielded wallet.
Or, you can buy a SignalVault card as seen on Shark Tank.

Shimming
A paper-thin shim goes in between the credit card reader and when you stick your card in, it collects the data.

Installing the shim is easy and it might be there for weeks collecting data.
Then they will use the data to create fake cards to make fraudulent purchases.
A way to detect this is when it’s a little harder to swipe than usual. So, If possible, try to avoid this payment and use the tap-to-pay option.
Sources:
Talking to Strangers by Malcolm Gladwell
It’s Not All About Me by Robin Dreeke



