Last Updated on November, 2023 by Edison
These days, having an online presence is a must, especially if you run a business. It has opened the door to a world full of opportunities.
But there’s a downside: It has also pushed us into a battle against a different class of criminals.
Growing up, we were taught to avoid certain individuals or locations, and we received guidance on handling difficult situations.
The online world is different. Here, the bad guys are not your average half-wit criminal you may encounter in the street.
Cybercriminals are usually intelligent, creative, and resilient people.
They also have a collection of sophisticated tools at their disposal. So, defending against them is a challenging task.
Here, I will cover how cybercriminals use social engineering to get the job done. By understanding their mindset and tactics, you can protect yourself from them.
Business Email Compromise
The BEC scam is when someone pretends to be the director and convinces an employee working at the Finance Department to send a wire transfer to the scammer’s account.
According to an FBI report, businesses have lost nearly $2.4 billion from BEC scams in 2021.
To understand how it works, let’s look at a real example….
A man named Onwuchekwa Kalu, living in Nigeria, stole $1.25 million from an investment firm in Boston, Massachusetts.
This firm is referred to as Company A in the court document.
In the past 12 years, Company A has invested in multiple businesses across North America, Europe, and Israel that focus on solving heart-related issues.
We also have Company B – a financial services company in London, which processed fund transfers for a bank account held by Company A at the Bank of NY Mellon.
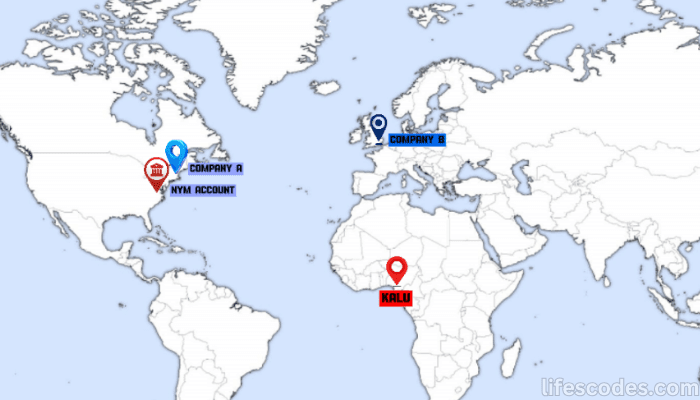
Map Image from FreeWorldMaps
Alright, here’s how the scam played out:
Kalu and his accomplices hacked into an employee’s email account at Company A and installed malware that forwarded every email containing the words Invoice, Fund, Pay, and Wire to an external email controlled by them. [george.morgan33333@gmail.com]

By looking at the emails, they figured out who was in charge of the money.
In this case, Company B.
You know, some corporations have their own finance department, while others hire a financial services firm to do it for them.
Then, they bought a domain name just one letter different from the Company’s actual website—something like CommpanyA.com with two Ms.
In my video, I showed how you can clone any site even if you have never done it before – of course, for security awareness purposes.
They used the domain name to make two fake email accounts for Company A’s directors.
DirectorA1@CommpanyA.com
DirectorA2@CommpanyA.com
Using these accounts, they emailed an employee at Company B.
They tricked him into transferring money from Company A’s NY Mellow account to a bank account in Mexico controlled by Kalu.

The pretext was to buy equipment from a Heart Monitor Company for the price of $625,000

When Employee B noticed the account number had changed, the scammers said the Heart Monitor Company had updated their banking information.
This convinced Employee B to go ahead with the transfer.
About a week later, they sent more emails to persuade Employee B to send another $625,000 to a different account in Mexico.

And this is how they managed to steal $1.25 million.
Fortunately, they were eventually caught and brought to the US for trial.
A More Sophisticated BEC Attack
As you can see, BEC scams are scarily effective. Although, they don’t get as much attention in the news as other attacks, like ransomware.
In addition, BEC scams have become more sophisticated with the development of technology.
Social engineers and scammers can use AI voice cloning tools to make the pretext more believable.
For instance, there’s a crazy case where cybercriminals pulled off a $35 million heist in the United Emirates using a combination of Business Email Compromise and AI voice cloning.
Let’s break it down quickly:
In 2020, a branch manager got a phone call that seemed to be from the company’s headquarters.
The caller sounded just like the company’s director, so the manager believed it was real.
He also got some related emails about this call.
The fake director said they wanted to buy a company and that a lawyer named Martin Zelner was in charge of the acquisition.
The manager got several emails from Zelner, including one with authorization from the Director.
This convinced the manager to send $35 million to several bank accounts.
Beirut
Corporations spend lots of money on network and information security.
And it’s a necessary expense—no doubt about it.
But what if a hacker could walk into the building, sit at a computer, and plug a malicious USB?
You would think security guards or other employees would notice the stranger among them. But sometimes they don’t.
That’s why companies hire physical pen testers like Jason E Street.
He tests whether someone unauthorized can enter the building and compromise the system.
Over 20 years, he’s done this kind of work worldwide.
But one of the most interesting stories is about a job he did for Société Générale Bank in Lebanon where he managed to compromise 3 branches of this bank and another bank by mistake.

I will analyze only the first branch, but if you want to know the entire story, I recommend listening to the episode of Darknet Diaries.
So how did he do it?
As soon as he walks into the place, he heads to a hallway with offices and stands right outside the manager’s door for 30 seconds.

This pause is important because he makes it look like he’s got a meeting with the manager.
I mean, who waits outside someone’s office for no reason, right?

Then he goes straight to the executive’s office, and her impression is that he talked to the manager.
Jayson explains he’s doing an audit on the computer systems and uses technical jargon to make the story more believable.
She falls for it and lets him plug a USB into the computer and even take pictures of the screen.

Within one minute, he had already compromised the system, but he didn’t stop there…
Since he has built credibility and authority in the eyes of other employees, he can waltz behind the tellers’ area and plug in that USB.
At this point, he pretty much does whatever he pleases in that branch.
You can achieve amazing results by correctly applying the most basic principles.
And I think what happened in Beirut embodies this observation.
Here’s why:
The first principle is authority.
From the start, he presented himself as an expert sent from headquarters to check the security in this branch.
When you think about it, It’s technically the truth. HE IS an expert sent to check the security of this branch.
When pretexting, you should use a story close to the truth because it makes lying easier.
Next, we have social proof.
The executive thinks he got permission from the manager; the bank tellers believe he got permission from the executive; the Same goes for the other departments.
Everyone thinks that the other guys have done their job of verifying him.
When, in fact, no one did.
Then we have the most essential element which is looking and sounding the part.
You know, most people operate on autopilot. So, when you blend into their environment… When you don’t give people a reason to suspect you are not who you say you are, they will continue with their day.
Why does this happen?
It’s because of a brain area called…
The Reticular Activating System
The RAS is an area that plays a crucial role in focusing your attention. It’s like a filter that focuses on important information while ignoring the less important stuff.
You know, the brain loves to save energy.
Once you do a task several times, like driving the car, pumping gas, or typing on your computer, you will learn to do it unconsciously.
The brain relies on imprinted memories to complete these tasks without consciously processing every detail.
So, every day, we do activities on autopilot to conserve energy.
The downside is that we often miss important details on what’s happening around us.
An interesting study showed that people failed to see money on the trees on the side of the road they were passing.
What does it mean for social engineers?
Most employees you will encounter during social engineering engagement are on autopilot mode.
They just do their role at work.
And if you do something that breaks their autopilot, the RAS will be activated, and they’ll pay attention. They will become curious and ask questions.
Now, how can you make yourself fit into their reality?
When you are creating a pretext, it’s not just playing a role… You need to become that person.
Every single detail about your character and environment matters.
- The clothing – What your characters wear
- Body language – The way your character walks and talks. But avoid using an accent unless you have mastered it.
- The Back story – If you are pretending to be a technician, you can give them a business card; if they call, your partner can answer and support your story.
- You should also consider small details. Would your character carry a magazine, newspaper, or briefcase? Avoid wearing a necklace cross ring or having a tattoo because those things draw people’s attention.
In addition, when building rapport with a target, using information from your life can help tap into those emotions and make you seem genuine.
For example, if you are trying to build rapport with someone with a daughter, don’t say you also have a daughter (if you haven’t), but you might have a niece, so use that information.
Get People to Open Up
People love to talk about themselves.
On average, they spend 60% of conversations talking about themselves, which goes up to 80% when communicating via social media.
There is a simple explanation behind this… It makes them feel great.
According to research by Harvard University, when people reveal personal information to others, there is activation in the mesolimbic dopamine system. The same area in the brain that becomes active when we receive food, sex, or money.
But there is more…
In another study, people were willing to accept 17% less money to talk about themselves.
Bottom Line: Their brain will not reward them if they don’t talk about themselves.
So, suspend your ego and focus the conversation on them. It’s amazing how much you can learn about a stranger simply by asking a few calibrated questions and listening.
Exploiting Empathy
Another powerful social engineering technique is putting the target into a heightened state of emotion. It can be empathy or fear.
When you do that, you dramatically reduce their ability to think logically.
So they become easier to manipulate.
In the video, How to Outsmart Emotional Vampires, I have explained in detail how this process works and how to prevent others from pushing your buttons.
But here I want to give you an example of a social engineer exploiting empathy to get what she wants.
It happened when the journalist Kevin Roose went to Defcon and challenged a team of hackers to hack him.
Now, let’s see the part where Jessica Clark (a social engineer) calls his phone provider with the goal of getting his email address.
After she spoofs his number, she plays a video with a background of a baby crying. She is apologetic and kind. She explains that they have been trying to get a loan and that she screwed up and made a reasonable request.
I mean, what customer support would suspect that she is not really his wife?
In a short time, she triggers empathy and a sense of urgency. And most importantly, she leaves no room for doubt that she’s not his wife.
Another example of using empathy to get the job done is from the book Unmasking the Social Engineer.
Christopher Hadnagy tells a story about an SE engagement.
The goal was to insert malicious software onto the company’s computer network using a USB key.
They wanted to test the corporate policy that forbids employees from inserting foreign devices into any company machine.
He was wearing a business suit and was holding a folder with a few “resumes.” As he parks the car, he spills coffee all over the folder.
Then, he enters the building with sadness displayed on his face.
He walks to the front desk, and the secretary asks, “Oh, no, honey. What happened?”
Chris quickly scanned her desk pictures and saw a small child with a cat.
“I’ve been out of work for a while, and I finally got an interview here today. I was driving here all nervous, and a cat ran out in front of me.
I love cats, and I didn’t want to hit it, so I swerved, and my coffee fell out of its holder onto my seat and drenched my resumes.
Fortunately, I missed the cat, but I killed my resumes.”
“Oh, that’s terrible. What can I do to help?”
“I have my resume on this USB key. Could you print me just one copy, please?”
And that was it. The job was done.
The Target Hack
In mid-December 2013, the DOJ informed Target that their system was being attacked.
Shocked by the notice, the executives immediately launched an internal investigation and found a breach of epic proportions – 40 million card details and 70 million customer details were stolen.
And as often happens… The breach was possible not because the attackers found a brilliant solution but because the defenders made many unforced errors.
So, how did Target get Hacked?
I’d recommend watching the part where I explain how the Target hack happened. I’ve included the link with the specific time.
Two months before the attack, they found a list of all the vendors working with Target on Google.
Then, they send malicious emails to all these vendors and see who would make the best entryway for Target’s systems.
They chose Fazio Mechanical – an HVAC business based in Pittsburg, Pennsylvania.
An employee of Fazio fell for the phishing email, allowing a malware called Citadel to infect the computer – Now, Citadel is used to steal login information.
It could’ve been detected, but Fazio’s biggest defence was a free version of Malwarebytes – which doesn’t detect malware unless you run it manually.
Through this employee, hackers could access the Targets Web Portal for the Vendors.
Once they were in, they exploited a vulnerability in the web application, giving them a backdoor to upload files and execute arbitrary OS commands.
In other words, by exploiting this portal, they were inside Target’s network.
A standard security approach is that when you build your network, you want to segment it so that different departments only have access to what they need.
In this case, there was no reason for a Vendor to access the internal corporate network.
This approach is based on the “Zero Trust” principle – No user or machine should be trusted, from inside or outside the network.
And it requires users to verify themselves continuously.
Once inside the network, they need to find the servers holding credit cards.
To get this info, they target Active Directory. It contains the data on all members of the domain – users, computers, and services.
Then, they can move laterally to the database where they stole the Personally Identifiable Information; next, they move to the most important system, POS machines.
They infect the machines in every target store with malware called Kaptoxa.
It’s a program that scrapes card information from POS machines running on Windows.
This was a huge blow for Target.
On top of the lost profits, because they were hacked near the holidays… Target lost $252M, while the insurance companies covered $90M from this sum.



